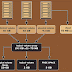
We can create Amazon VPC by using the following steps:
- Create a VPC
- Create an Internet Gateway (IGW)
- Attach IGW to VPC
- Create Two Subnets:
Public Subnet (Subnet-1) and Private Subnet (Subnet-2) - Enable Auto-assign IP settings for Public Subnet
- Create a Route Table and associate to subnet-1
- Create Tow Instances:
Web Server (First instance for public subnet) and DB Server (Second instance for private subnet) - Verify internet access on web server
- Create a NAT Gateway
- Create a Route table for NAT Gateway and associate to Subnet-2
- Verify internet access on DB server.
 |
| AWS VPC Struct |
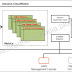
Step 1: Create a VPC:
As VPC is a region-specific service, first we need to make sure in which region we are creating VPC. In this practical, we are creating a VPC in North Virginia Region for a web solution company, named 'websol'. One default VPC is also running there. So, I suggest, do not delete or change inside default VPC. Create your own VPC named 'websol-vpc'.AWS ➔ Services➔ VPC ➔ Your VPCs ➔ Create VPC ➔ Name tag: websol-vpc ➔ IPv4 CIDR block: 10.0.0.0/16 ➔ [*] No IPv6 CIDR Block ➔ Tenancy: default ➔ Create ➔ Close.
This will create a new VPC named 'websol-vpc' in North Virginia region.
Step 2: Create an Internet Gateway (IGW):
AWS ➔ Services ➔ VPC ➔ Internet Gateways ➔ Create Internet Gateway ➔ Name tag: websol-igw ➔ Create ➔ Close.Step 3: Attach IGW to VPC:
AWS ➔ Services ➔ VPC ➔ Internet Gateways ➔ Select 'websol-igw' gateway ➔ Actions ➔ Attach to VPC ➔ VPC: Select 'websol-vpc' ➔ Attach.In the state section, we can verify that Internet Gateway 'websol-igw' is attached to 'websol-vpc' VPC.
Step 4: Create Two Subnets:
- Create the first Subnet for Web Server:
AWS ➔ Services ➔ VPC ➔ Subnets ➔ Create subnet ➔ Name tag: websol-sub1-pub ➔ VPC: websol-vpc ➔ Availability Zone: us-east-1a ➔ IPv4 CIDR block: 10.0.1.0/24 ➔ Create ➔ Close.
- Create the second Subnet for Database Server:
AWS ➔ Services ➔ VPC ➔ Subnets ➔ Create subnet ➔ Name tag: websol-sub2-pvt ➔ VPC: websol-vpc ➔ Availability Zone: us-east-1b ➔ IPv4 CIDR block: 10.0.2.0/24 ➔ Create ➔ Close.
Step 5: Enable Auto-Assign IP settings for public subnet:
AWS ➔ Services ➔ VPC ➔ Subnets ➔ Select Subnet 'websol-sub1-pub' ➔ Actions ➔ Modify auto-assign IP settings ➔ [*] Enable auto-assign public IPv4 address ➔ Save.Step 6: Create a Route Table and associate to subnet-1:
- Create a route table to get attached IGW to subnet1, which belongs to Web Server:
AWS ➔ Services ➔ VPC ➔ Route Tables ➔ Create Route Table ➔ Name tag: websol-rt-pub ➔ VPC: websol-vpc ➔ Create ➔ Close.
- Make Route Entries:
AWS ➔ Services ➔ VPC ➔ Route Tables ➔ Select 'websol-rt-pub' Route Table ➔ Routes ➔ Edit routes ➔ Destination: 0.0.0.0/0 ➔ Target: 'websol-igw' ➔ Save routes ➔ Close.
- Associate Route Table to Subnet-1:
AWS ➔ Services ➔ VPC ➔ Route Tables ➔ Select 'websol-rt-pub' Route Table ➔ Subnet Associations ➔ Edit Subnet Associations ➔ Select 'websol-sub1-pub' subnet ➔ Save.
Step 7: Create Instances:
Create two instances; one for Web Server in Subnet-1 and another instance for Database Server in Subnet-2.
- Create first instance in Subnet-1 named 'win-web-srv':
AWS ➔ Services ➔ EC2 ➔ Instances ➔ Launch Instance ➔ [*] Free Tier only ➔ Select 'windows Server 2008' AMI ➔ Instance Type: t2.micro ➔ Next ➔ Number of instances: 1 ➔ Network: select own created 'websol-vpc' VPC ➔ Subnet: As we are creating this instance for subnet-1, which we are using for a web server, select us-east-1a ➔ Auto-assign Public IP: We have already enable auto-assign in subnet, so there is no need to change this ➔ Next ➔ Next: tags ➔ Name: win-web-srv ➔ Next: SG ➔ [*] Create a new Security Group ➔ Security group name: win-sg ➔ Description: win-sg is created to access windows instances ➔ Rule ➔ RDP: TCP: 3389: Anywhere ➔ Add Rule ➔ HTTP: TCP: 80: Anywhere ➔ Add Rule ➔ HTTPS: TCP: 443: Anywhere ➔ Review and Launch ➔ Launch ➔ Create a new key-pair OR select any existing key pair ➔ Launch Instances ➔ View Instances.
- Create second instance in Subnet-2 named 'win-db-srv':
AWS ➔ Services ➔ EC2 ➔ Instances ➔ Launch Instance ➔ [*] Free Tier only ➔ Select 'windows Server 2008' AMI ➔ Instance Type: t2.micro ➔ Next ➔ Number of instances: 1 ➔ Network: select own created 'websol-vpc' VPC ➔ Subnet: As we are creating this instance for subnet-2, which we are using for a Database Server, select us-east-1b ➔ no need for enabling Auto-assign Public IP as we are creating this instance for private subnet ➔ Next ➔ Next: tags ➔ Name: win-db-srv ➔ Next: SG ➔ [*] Create a new Security Group ➔ Security group name: win-db-sg ➔ Description: win-db-sg is created to access windows DB instances ➔ Rule ➔ RDP: TCP: 3389: Custom: 10.0.0.0/16 (here, we gave CIDR for security purposes) ➔ Review and Launch ➔ Launch ➔ Create a new key-pair OR select any existing key pair ➔ Launch Instances ➔ View Instances.
- Generate passwords of both instances and copy them in notepad:
For Web Server:
AWS ➔ Services ➔ Instances ➔ Select Instance 'win-web-srv' ➔ Actions ➔ Get Windows Password ➔ Browse ➔ (Provide Private IP) ➔ Decrypt Password ➔ Copy this password in notepad.
For DB Server:
AWS ➔ Services ➔ Instances ➔ Select Instance 'win-db-srv' ➔ Actions ➔ Get Windows Password ➔ Browse ➔ (Provide Private IP) ➔ Decrypt Password ➔ Copy this password in notepad.
Step 8: Verify internet access on Web Server:
Run ➔ type 'mstsc' ➔ Computer: paste public IP from EC2 Dashboard ➔ Connect ➔ Username: Administrator ➔ Password: Paste from notepad, where we saved it ➔ Connect ➔ (this will login us to our web-server instance) ➔ Run ➔ cmd ➔ type 'ping www.google.com' ➔ If we get a reply, means we got the connection.
Step 9: Create a NAT Gateway:
AWS ➔ Services ➔ VPC ➔ NAT Gateways ➔ Create NAT Gateway ➔ Subnet: Select public subnet 'websol-sub1-pub' ➔ Elastic IP Allocation ID: Click on Create New EIP (this will assign and allocate a Public Elastic IP to NAT Gateway) ➔ Create a NAT Gateway ➔ Close.
Allow some moments to get the status from pending to available, because NAT Gateway takes some time to create.
Step 10: Create Route Table for NAT Gateway and Associate to Subnet-2:
- Create a route table to get attached with NAT Gateway:
AWS ➔ Services ➔ VPC ➔ Route Tables ➔ Create Route Table ➔ Name tag: websol-rt-nat ➔ VPC: websol-vpc ➔ Create ➔ Close.
- Make Route Entries:
AWS ➔ Services ➔ VPC ➔ Route Tables ➔ Select 'websol-rt-nat' Route Table ➔ Routes ➔ Edit routes ➔ Destination: 0.0.0.0/0 ➔ Target: Select NAT Gateway ➔ Save routes ➔ Close.
- Associate Route Table to Subnet-2:
AWS ➔ Services ➔ VPC ➔ Route Tables ➔ Select 'websol-rt-nat' Route Table ➔ Subnet Associations ➔ Edit Subnet Associations ➔ Select 'websol-sub2-pvt' subnet ➔ Save.
Step 11: Verify internet access on DB server:
- First login to the web-server:
Run ➔ type 'mstsc' ➔ Computer: paste public IP of web-server from EC2 Dashboard ➔ Connect ➔ Username: Administrator ➔ Password: Paste from notepad, where we saved it ➔ Connect ➔ this will login us to our web-server instance.
- Open RDP from the web server and login to the DB-Server using private IP:
In Web-Server ➔ Run ➔ type 'mstsc' ➔ Computer: paste private IP of DB-server from EC2 Dashboard ➔ Connect ➔ Username: Administrator ➔ Password: Paste from notepad, where we saved it ➔ Connect ➔ this will login us to our DB-Server ➔ Open Run ➔ type command 'cmd' ➔ ping www.google.com.
ACCESS GRANTED…ENJOY!!!
CLEANUP:
- Terminate both instances
- Delete NAT Gateway
- Release Elastic IP which we used in NAT gateway
- Delete VPC
Step 1: Terminate both instances:
AWS ➔ Services ➔ EC2 ➔ Instances ➔ Select both instances ➔ Action ➔ Instance State ➔ Terminate.
Step 2: Delete NAT Gateway:
AWS ➔ Services ➔ VPC ➔ NAT Gateways ➔ Select NAT Gateway ➔ Actions ➔ Delete NAT Gateway ➔ Delete NAT Gateway.
Again this will take some time to be deleted as it took at the time of creation.
Step 3: Release Elastic IP which we used in NAT Gateway:
AWS ➔ Services ➔ VPC ➔ Elastic IPs ➔ Select Elastic IP ➔ Actions ➔ Release addresses ➔ Release.
Step 4: Delete VPC:
AWS ➔ Services ➔ VPC ➔ Your VPCs ➔ Select your own created VPC (not default) ➔ Actions ➔ Delete VPC ➔ Delete VPC ➔ Close.

Good job...
ReplyDeleteThanks Bikash (y)
DeleteGood explanation
ReplyDeleteThanks Divakar.. I got first Lab working..
ReplyDeleteOk buddy!
DeleteSoon I am going to upload docs about VPC-Endpoints. Be in touch.
Thanks.
Thanks. GOOD job
ReplyDeleteGood Job...
ReplyDeleteAwesome
ReplyDeleteGreat initiative from you side
ReplyDeleteI am amar and i am working as devops/cloud admin (aws/gcp) with kubernetes clustering setup cloud as well as om premise solutions , so please let me know if i can also contribute some thing on you initiative so others may get help.
Thanks Amar!
DeleteIt's really grateful. Kindly provide me any of your contact information. My email ID is divakar.rastogi@gmail.com.
Thanks for sharing this information to us.from this topic i got some knowledge.
ReplyDeleteBest aws training in ameerpet| aws training in hyderabad
Thank you for sharing useful information with us to get some idea about that content.
ReplyDeleteGoogle Cloud Platform Training
GCP Online Training
Google Cloud Platform Training In Hyderabad
Good one thanks
ReplyDeleteI like this post.Thanks for sharing.
ReplyDeleteGoogle Cloud Platform Training
GCP Online Training
Google Cloud Platform Training In Hyderabad
have you included practical on VM migration on AWS?
ReplyDeleteThanks Divakar for sharing..
ReplyDeleteFree Software Cracked Software, Backlinks, Tips&Tricks
ReplyDeleteSpotify Free Premium Accounts
Zee5 Premium Accounts
Amazon prime Username And Passwords
netflix username and passwords
Thanks For sharing this Superb article.I use this Article to show my assignment in college.it is useful For me Great Work. https://www.sorrisieservizi.it/internet/vpn-sicura-e-gratuita/
ReplyDelete