VPC Peering:
VPC peering can be used to create secure connectivity and resource sharing between two VPCs. A VPC peering connection helps us to facilitate the transfer of data. For example, if we have more than one AWS account, we can peer the VPCs across those accounts to create a file-sharing network. We can also use a VPC peering connection to allow other VPCs to access resources you have in one of our VPCs.
NOTE: VPC Peering is non-transitive.
Why we need VPC Peering:
- To avoid the use of the internet.
- Negligible Cost (If not using the internet, then we will not pay for this)
- Better speed
- Private IP could not travel on the Internet.
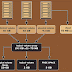
VPC Peering in the same region:
In this case, we have a VPC, which is for 'bank-a' in N. Virginia region with the following details:
- Region : N. Virginia
- VPC Name : bank-a-vpc
- Internet Gateway : bank-a-igw
- Subnets : 'bank-a-sub1-pub' and 'bank-a-sub2-pvt'
- Instances' Name : 'bank-a-webserver' and 'bank-a-dbserver'
- CIDR : 10.0.0.0/16
We have one more VPC, which is for 'bank-b' in N. Virginia region with the following details:
- Region : N. Virginia
- VPC Name : bank-b-vpc
- Internet Gateway : bank-b-igw
- Subnets : 'bank-b-sub1-pub' and 'bank-b-sub2-pvt'
- Instance Name : 'bank-b-webserver' and 'bank-b-dbserver'
- CIDR : 172.16.0.0/16
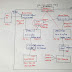
Steps, we need to follow to do VPC Peering in the same region:
- Create VPC peering connection at bank-a account
- Accept request from bank-b account
- Create a route entry in bank-a account
- Create a route entry in bank-b account
- Verify the access of bank-b-dbserver using its private IP
- Delete public subnet, route table, IGW and terminate instance named 'bank-b-webserver' from bank-b account
Step 1: Create VPC Peering connection at 'bank-a' account and send a request to 'bank-b':
AWS ➔ Services ➔ VPC ➔ Peering Connections ➔ Create Peering Connections ➔ Peering connection name tag: bank-a-to-bank-b ➔ VPC (Requester): bank-a-vpc ➔ Select another VPC to pear with ➔ Account: My Account ➔ Region: This Region ➔ VPC (Accepter): bank-b-vpc ➔ Create Peering Connection ➔ OK.
Step 2: Accept request from 'bank-b' account:
AWS ➔ Services ➔ VPC ➔ Peering Connections ➔ Actions ➔ Accept Request ➔ Verify Details ➔ Yes, Accept ➔ Close.
Step 3: Create route entries in 'bank-a' account as a 'Requester':
Here, we make an entry in both route tables
- In bank-a public route table and
- In bank-a default route table
- Make route entry in public route table of 'bank-a':
AWS ➔ Services ➔ VPC ➔ Route Tables ➔ In Search bar type 'bank-a' and hit enter to get bank-a route tables ➔ (1) Select bank-a-pub-rt ➔ Routes ➔ Edit routes ➔ Add route ➔ Destination: 172.16.0.0/16 ➔ Target: Peering Connection: bank-a-to-bank-b ➔ Save routes ➔ Close.
- Make route entry in the default route table of 'bank-a':
AWS ➔ Services ➔ VPC ➔ Route Tables ➔ (2) Select bank-a default RT ➔ Routes ➔ Edit routes ➔ Add route ➔ Destination: 172.16.0.0/16 ➔ Target: Peering Connection: bank-a-to-bank-b ➔ Save routes ➔ Close.
Step 4: Create route entry in 'bank-b' account:
In this case, we make an entry only in default route table of bank-b:
AWS ➔ Services ➔ VPC ➔ Route Tables ➔ (2) Select bank-b default RT ➔ Routes ➔ Edit routes ➔ Add route ➔ Destination: 10.0.0.0/16 ➔ Target: Peering Connection: bank-a-to-bank-b ➔ Save routes ➔ Close.
Step 5: Verify the access of bank-b-dbserver using its private IP:
- Login to instance named 'bank-a-webserver'
- From inside this 'bank-a-webserver' access bank-b-dbserver using its private IP
GET ACCESS…ENJOY!!!
Step 6: DELETE PUBLIC SUBNET, PUBLIC ROUTE TABLE, IGW AND TERMINATE INSTANCE NAMED 'bank-b-webserver' FROM BANK-B ACCOUNT
As there is no further need for these attributes, we can delete them. But if in the future, we want to have a NAT Gateway on DB Server, then we need to create an IGW and a public subnet again.
- Terminate the instance named 'bank-b-webserver':
AWS ➔ Services ➔ EC2 ➔ Instances ➔ Select instance named 'bank-b-webserver ➔ Actions ➔ Instance State ➔ Terminate.
- Delete public subnet of Bank-b:
AWS ➔ Services ➔ VPC ➔ Subnets ➔ Select public subnet of Bank-b ➔ Actions ➔ Delete Subnet ➔ Verify Delete Subnet ➔ Close.
- Delete public route table of 'bank-b':
AWS ➔ Services ➔ VPC ➔ Route Tables ➔ Select public route table of bank-b ➔ Actions ➔ Delete Route Table ➔ Verify Delete Route Table ➔ Close.
- Delete IGW created for 'bank-b':
AWS ➔ Services ➔ VPC ➔ Internet Gateways ➔ Select IGW created for 'bank-b' ➔ Actions ➔ Detach from VPC ➔ Delete Internet Gateway ➔ Verify ➔ Close.
Note: Even we deleted this, then too DB-Server of 'bank-b' will get connected to the Web Server of 'bank-a'.

No comments:
Post a Comment