There are two things TRUSTING ACCOUNT and TRUSTED ACCOUNT in which we could confuse. So, first, understand this.
 |
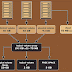
| Fig: AWS Cross Accounts Access Using IAM Roles |
Trusting Account:
Trusting Account means the company which has trust in another company and providing some users of a trusted company to perform some specific tasks.Trusted Account:
Trusted Account means the company, which is trusted by another company.Suppose, you want to access some resources of your friend’s account (for e.g. you want to access IAM and S3 by your friend’s AWS account). As he is allowing you to access to his account; his account is TRUSTING ACCOUNT and as you are trusted by him, so, your account is TRUSTED ACCOUNT.
In other words, we can say that the account which is providing services to access is known as TRUSTING ACCOUNT and the account which is using services is known as TRUSTED ACCOUNT.
For example; you have your own AWS account as 'user1' which have account ID '123456789012' (Trusted Account) and your friend has another AWS account as 'frnd1' which has account ID '987654321098' (Trusting Account).
In your company whose root user is 'user1' there are some users who want to access your friend’s account. We will add all of them in a group named 'POC'.
Your friend’s account needs to provide some limited access to the users of your company without sharing any username, password, access key, and secret access key. For this, he will use Roles.
Types of Role:
1. Service Link Role (we have used in Replication)2. Service to service Role (e.g. ec2 to s3)
3. Cross Account Role (users from other AWS accounts)
4. Federation Based Role (allow access to AD users or LDAP users)
Here, your friend needs to use Cross-Account Role.
PRACTICAL:
Make sure for this practice, we are going to use two browsers, For example:IN CHROME, LOGIN WITH YOUR OWN AWS ACCOUNT and
IN MOZILLA FIREFOX, LOGIN WITH YOUR FRIEND’S AWS ACCOUNT
First, we are working with TRUSTING ACCOUNT (which is your friend’s account in Mozilla Firefox):
Create a Cross Account Role:
AWS ➔ Services ➔ IAM ➔ Roles ➔ Create Role ➔ Another AWS Account ➔ Account ID: Trusted Company's Account Number (in this e.g. your account number) ➔ Next Permission ➔ S3ReadOnly + EC2ReadOnly ➔ Next: Tags ➔ Next: Review ➔ Role Name: my_cross_account_role ➔ Create Role.
Verify that the role is created. Copy this new created Role Name and Role ARN to the notepad.
Now, Trusting part is done.
Second, we will work with TRUSTED ACCOUNT (which is your own account in Chrome):
Create a User:
AWS ➔ Services ➔ IAM ➔ Users ➔ User Name: Sandy ➔ Access Type: AWS Management Console access ➔ Console password: Custom Password: redhat ➔ Untick Require password reset ➔ Next: Permission ➔ Next: Tags ➔ Next: Review ➔ Create User ➔ Close.Create a Group:
AWS ➔ Services ➔ IAM ➔ Groups ➔ Create New Group ➔ Group Name: POC (Proof of Concepts) ➔ Next Step ➔ Next Step ➔ Create Group.Add Selected Users to this Group:
AWS ➔ Services ➔ IAM ➔ Groups ➔ POC ➔ Users ➔ Add User to Group ➔ [*] sandy ➔ Add User.Create a Policy:
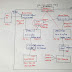
AWS ➔ Services ➔ Create Policy ➔ Choose a Service: STS (Secure Token Service) ➔ Actions: Access Level ➔ Expend All ➔ [*] Assume Role ➔ Resources: Specific ➔ Add ARN ➔ Account: ARN of TRUSTING ACCOUNT’s Role ➔ Add ➔ Review Policy ➔ Name: AssumeRolePolicy ➔ Create Policy. |
| Fig: To Create a Policy |
Attach this policy to the Group (POC):
AWS ➔ Services ➔ IAM ➔ Policies ➔ Search and select AssumeRolePolicy ➔ Policy Usage ➔ Attach ➔ Attach to group POC ➔ Attach Policy.TO VERIFY:
Copy URL from Dashboard of Trusted Account and run it on browser and login in AWS by user sandy.Go to the username as the third last option of menu bar ➔ Switch Role ➔ Account: Trusting Company’s Account Number ➔ Role: Trusting Company’s Role Name ➔ Switch Role ➔ ACCESS GRANTED as RoleName@AccountNumber.
Enjoy!
No comments:
Post a Comment